Hello
I coded as follows in ASP.NET.
Response.Redirect("http://www.ulsanpe.com:70/Default.aspx?id=" + id + "&password=" + pw);
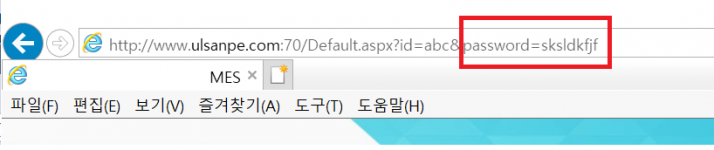
Below is the resulting image.

ASP.NET ===> Response.Redirect("http://www.ulsanpe.com:70/Default.aspx?id=" + id + "&password=" + pw);
Questions 1) In this case, how do you usually pass the password part as a parameter of Response.Redirect?
Questions 2) When I move to a new web page, I have to pass ID and password as parameters. Are there other ways other than this one(Response.Redirect)?
please answer
I coded as follows in ASP.NET.
Response.Redirect("http://www.ulsanpe.com:70/Default.aspx?id=" + id + "&password=" + pw);
Below is the resulting image.
ASP.NET ===> Response.Redirect("http://www.ulsanpe.com:70/Default.aspx?id=" + id + "&password=" + pw);
Questions 1) In this case, how do you usually pass the password part as a parameter of Response.Redirect?
Questions 2) When I move to a new web page, I have to pass ID and password as parameters. Are there other ways other than this one(Response.Redirect)?
please answer
Attachments
Last edited by a moderator: